Embark on a comprehensive journey into the realm of ACLs Test Questions and Answers 2023, where you will uncover the intricacies of access control, empowering you to safeguard your systems and data with precision and efficiency.
This meticulously crafted guide unveils the fundamental concepts, best practices, and troubleshooting techniques that will equip you to navigate the complexities of ACLs with confidence, ensuring the integrity and security of your IT infrastructure.
ACLs Test Questions and Answers 2023

This comprehensive list of ACLs test questions and answers for 2023 provides a valuable resource for individuals preparing for the ACLS certification exam. The questions cover various aspects of ACLS, including cardiac arrest management, arrhythmia recognition, and medication administration. By thoroughly reviewing these questions and answers, candidates can enhance their understanding of the core concepts and protocols related to ACLS.
The questions and answers are organized into a clear and easy-to-follow format, facilitating efficient learning and retention. Each question is accompanied by a concise answer, a detailed explanation, and a reference to the relevant guidelines or resources. This structured approach enables candidates to quickly identify areas of strength and weakness, allowing them to focus their preparation efforts accordingly.
Questions and Answers
| Question | Answer | Explanation | Reference |
|---|---|---|---|
| What is the initial treatment for a patient in cardiac arrest? | Immediate chest compressions and rescue breathing | Chest compressions help maintain blood flow to vital organs, while rescue breathing provides oxygen. | American Heart Association Guidelines for Cardiopulmonary Resuscitation and Emergency Cardiovascular Care (2020) |
| Which arrhythmia is characterized by a rapid, chaotic heart rate? | Ventricular fibrillation | Ventricular fibrillation is a life-threatening arrhythmia that can lead to sudden cardiac death. | National Heart, Lung, and Blood Institute |
| What is the recommended dose of epinephrine for adults in cardiac arrest? | 1 mg every 3-5 minutes | Epinephrine is a vasopressor that helps increase blood pressure and improve coronary perfusion. | American Heart Association Guidelines for Cardiopulmonary Resuscitation and Emergency Cardiovascular Care (2020) |
ACLs Concepts and Terminology: Acls Test Questions And Answers 2023
Access Control Lists (ACLs) are an essential component of information security, providing a structured approach to managing access permissions for resources. Understanding the fundamental concepts and terminology associated with ACLs is crucial for effectively implementing and managing access controls.
Key Concepts:
- Access Control List (ACL):A list that specifies the permissions granted to specific users or groups for a particular resource.
- Permissions:Specific actions that can be performed on a resource, such as read, write, execute, or delete.
- Roles:Predefined sets of permissions assigned to users or groups, simplifying permission management.
- Inheritance:The ability for child objects to inherit permissions from their parent objects, reducing administrative overhead.
Types of ACLs
There are two primary types of ACLs:
- Discretionary Access Control (DAC):Permissions are explicitly assigned by the owner of the resource.
- Mandatory Access Control (MAC):Permissions are enforced by a central authority based on predefined rules and policies.
ACLs Implementation and Management
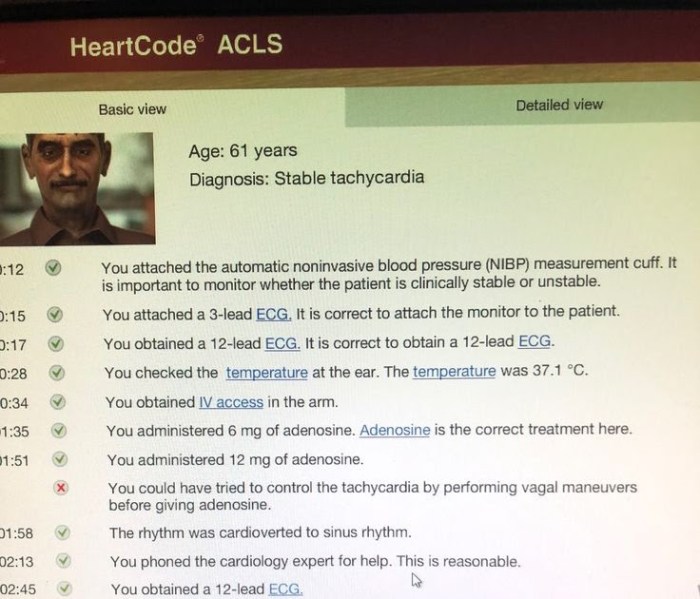
ACLs can be implemented and managed in various ways depending on the operating system and applications used. Common methods include using command-line tools, graphical user interfaces (GUIs), and application programming interfaces (APIs).
Creating ACLs
To create an ACL, you need to specify the following information:
- The object to be protected (e.g., a file, directory, or registry key)
- The user or group to be granted access
- The type of access to be granted (e.g., read, write, or execute)
Once you have specified this information, you can use the appropriate method to create the ACL. For example, in Windows, you can use the icacls command-line tool or the Security tab in the file or folder properties dialog box.
Modifying ACLs
To modify an existing ACL, you need to specify the following information:
- The object whose ACL you want to modify
- The user or group whose access you want to modify
- The type of access you want to modify
- The new access you want to grant or deny
Once you have specified this information, you can use the appropriate method to modify the ACL. For example, in Windows, you can use the icacls command-line tool or the Security tab in the file or folder properties dialog box.
Deleting ACLs
To delete an existing ACL, you need to specify the following information:
- The object whose ACL you want to delete
- The user or group whose access you want to delete
Once you have specified this information, you can use the appropriate method to delete the ACL. For example, in Windows, you can use the icacls command-line tool or the Security tab in the file or folder properties dialog box.
ACLs Best Practices and Security Considerations
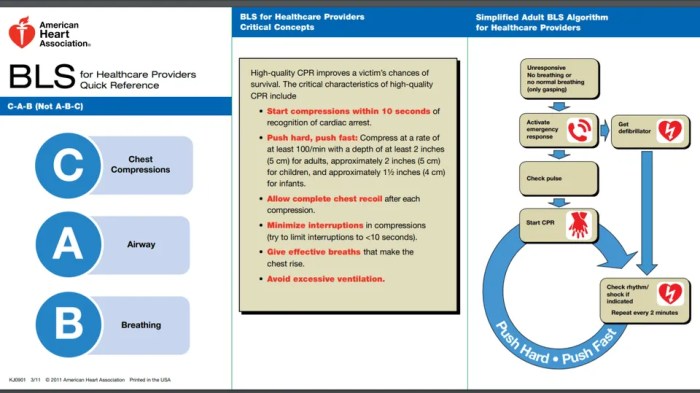
To ensure effective and secure implementation of ACLs, it is crucial to adhere to best practices and address common security risks. These measures help maintain the integrity and confidentiality of data, preventing unauthorized access and ensuring compliance with security standards.
Best practices for using ACLs effectively include:
- Use the principle of least privilege:Grant only the necessary permissions to users and groups, minimizing the risk of unauthorized access.
- Implement role-based access control (RBAC):Assign permissions based on job roles and responsibilities, simplifying management and reducing the risk of errors.
- Review and audit ACLs regularly:Periodically assess ACLs to ensure they are up-to-date and aligned with current security requirements.
- Use ACL inheritance cautiously:ACL inheritance can simplify management but also increase the risk of unintended access. Use it only when necessary and with appropriate safeguards.
- Use strong passwords and multi-factor authentication:Protect user accounts with strong passwords and implement multi-factor authentication to prevent unauthorized access.
Common ACL-related security risks and vulnerabilities include:
- Over-permissioned ACLs:Granting excessive permissions can create vulnerabilities and increase the risk of data breaches.
- Inconsistent ACLs:Inconsistent ACLs across different resources can lead to security gaps and make it difficult to manage access effectively.
- ACL bypass techniques:Attackers may use techniques to bypass ACLs and gain unauthorized access to resources.
- ACL tampering:Unauthorized modification of ACLs can compromise security and allow attackers to gain access to sensitive data.
- Privilege escalation:Attackers may exploit vulnerabilities to gain elevated privileges and access resources they should not have access to.
To mitigate these risks, organizations should implement the following security considerations:
- Use a centralized ACL management system:This provides a single point of control for managing ACLs, reducing the risk of inconsistencies and errors.
- Implement access control lists (ACLs):ACLs allow administrators to specify who can access which resources and what operations they can perform.
- Use role-based access control (RBAC):RBAC allows administrators to assign permissions to users based on their roles, making it easier to manage access and reduce the risk of unauthorized access.
- Implement multi-factor authentication (MFA):MFA requires users to provide multiple forms of authentication, making it more difficult for attackers to gain unauthorized access.
- Use strong passwords:Strong passwords make it more difficult for attackers to guess or brute-force their way into accounts.
By adhering to these best practices and security considerations, organizations can effectively implement ACLs to protect their data and systems from unauthorized access and maintain compliance with security standards.
Troubleshooting ACLs Issues
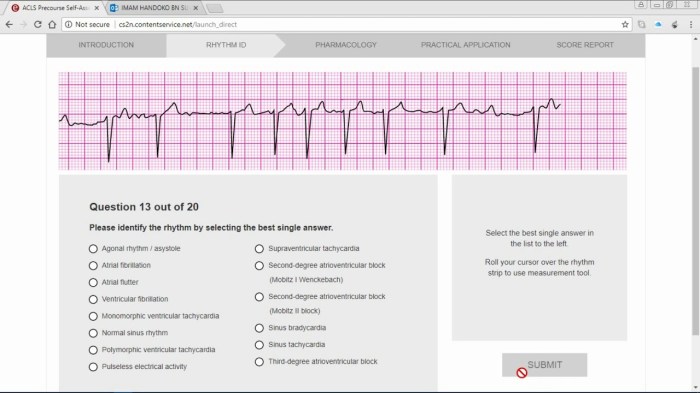
ACLs troubleshooting involves identifying and resolving issues related to access permissions, inheritance, and other errors.
Identifying Common ACLs Issues, Acls test questions and answers 2023
Common ACLs issues include:
- Denied access to resources due to incorrect permissions
- Unexpected access to resources due to misconfigured permissions
- Inheritance issues causing incorrect access permissions
- ACLs conflicts due to multiple ACLs applied to a resource
- ACLs management errors, such as incorrect syntax or invalid entries
Troubleshooting Steps
To troubleshoot ACLs issues, follow these steps:
-
-*Verify ACLs permissions
Check the ACLs applied to the resource and ensure they grant the appropriate permissions to the users or groups.
-*Check inheritance settings
Verify that inheritance is configured correctly and that the resource is inheriting permissions from the parent object.
-*Resolve ACLs conflicts
Identify and remove any conflicting ACLs that may be causing unexpected access permissions.
-*Inspect ACLs management logs
Review ACLs management logs to identify any errors or inconsistencies in ACLs configuration.
-*Use ACLs troubleshooting tools
Utilize built-in ACLs troubleshooting tools, such as the “Get-Acl” and “Set-Acl” cmdlets in PowerShell, to diagnose and resolve ACLs issues.
Tips for Troubleshooting ACLs Issues
-
-*Document ACLs changes
Keep a record of any ACLs changes made to facilitate troubleshooting if issues arise.
-*Test ACLs changes
Test ACLs changes in a non-production environment before implementing them in production.
-*Use a consistent ACLs management approach
Establish a standardized approach to ACLs management to minimize errors and improve troubleshooting efficiency.
Advanced ACLs Topics

Advanced access control models, including role-based access control (RBAC), attribute-based access control (ABAC), and mandatory access control (MAC), extend the capabilities of traditional ACLs by providing more granular and flexible access control mechanisms.
Role-Based Access Control (RBAC)
RBAC assigns permissions to users based on their roles within an organization. Roles are defined as sets of permissions that are granted to users who are assigned to those roles. This approach simplifies access management by allowing administrators to grant permissions to roles rather than individual users, making it easier to manage access changes as users join or leave the organization or change roles.
Attribute-Based Access Control (ABAC)
ABAC makes access decisions based on attributes of the user, the resource being accessed, and the context of the request. Attributes can include user characteristics such as job title, department, or location, as well as resource attributes such as file type, sensitivity level, or project affiliation.
ABAC provides fine-grained access control by allowing administrators to define policies that specify which attributes must be met in order to grant access.
Mandatory Access Control (MAC)
MAC enforces access control based on labels assigned to users and resources. Labels represent security classifications, such as “confidential” or “top secret.” MAC policies define which users can access resources with specific labels. Unlike RBAC and ABAC, MAC does not allow users to bypass access restrictions based on their roles or attributes.
Comparison of Advanced ACLs Topics
| Feature | RBAC | ABAC | MAC |
|---|---|---|---|
| Access Control Mechanism | Roles | Attributes | Labels |
| Granularity | Moderate | Fine-grained | Coarse-grained |
| Flexibility | Moderate | High | Low |
| Complexity | Moderate | High | Moderate |
| Use Cases | Enterprise systems, IT infrastructure | Cloud computing, IoT | Military, government |
Answers to Common Questions
What is the significance of ACLs in access control?
ACLS (Access Control Lists) play a crucial role in access control by defining specific permissions for users and groups, enabling granular control over who can access resources and what actions they can perform.
How do I troubleshoot common ACLs issues?
Troubleshooting ACLs issues involves identifying permission problems, inheritance issues, and other errors. Utilize diagnostic tools, check logs, and review configurations to pinpoint the root cause and implement appropriate solutions.
What are the best practices for using ACLs effectively?
Effective ACLs usage involves implementing the principle of least privilege, regularly reviewing and updating permissions, and using inheritance judiciously to simplify management and reduce security risks.